14) which of the following are breach prevention best practices
Identity sensitive data collected stored transmitted or processes. Which of the following are examples of personally identifiable information PII.

Cybersecurity Ot A Comprehensive Guide
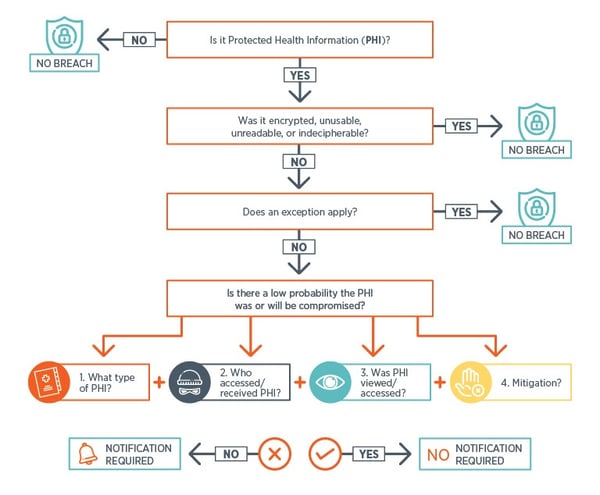
Which of the following statements about the HIPAA Security Rule are true.
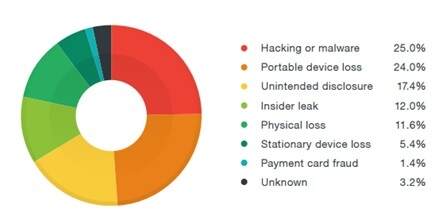
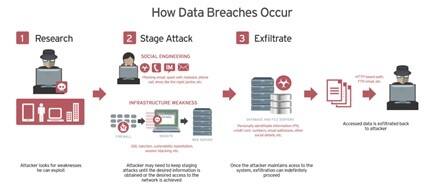
. To protect its data a business must first understand what and where it is -- necessitating a thorough inventory of all. Making weak passwords can be a reason for Data Breaches. Here are 10 best practices that organizations can use when developing data breach prevention methods and incident response plans.
The following are high-level best practices for preventing breaches. All of the above. Inventory all data sets and identify locations of sensitive information.
Access only the minimum amount of PHIpersonally identifiable information PII necessary B. While incident response policies tools and practices should also be part of an enterprises overall security posture the following tips focus on data breach prevention. Which of the following are true statements about limited data sets.
Promptly retrieve documents containing PHIPHI from the printer D. All of the above. So you have to create solid and high-end passwords for your data.
Which of the following are breach prevention best practices. He recommends campuses have firewalls. Which of the following are breach prevention best practices.
They need to be secure at the host eg. What are some best security practices to protect against data leakage. Create a strong password policy and enforce it.
In which of the following circumstances must an individual be given the opportunity to agree or object to the use and disclosure of their PHI. Remediation Accessed N PHI transmitted orally PHI on paper PHI transmitted electronically correct All of the above-----11 Which of the following are breach prevention best practices. Public Health Nigeria Public Health Nigeria an Interdisciplinary public health movement focused on health education advancing fair public health policies promoting fitness healthy diets responsible behavior community health and general wellbeing.
Implementing encryption standards and backup policies to decrease risks and make sure that software is up-to-date and patched regularly is vital to limiting the vulnerability of networks. Logoff or lock your workstation when it is unattended. A single technology cannot provide complete protection.
Identify all sensitive data. Established a national set of standards for the protection of PHI that is created received maintained or transmitted in electronic media by a HIPAA covered entity CE or business associate BA b. Convene a workgroup to research threats vulnerabilities.
Cybercriminals target non-public personal. The following are breach prevention best practices. Invest in security automation.
10 The HIPAA Security Rule applies to which of the following. Evaluate the risk of third-parties. All of this above.
Monitor the security posture of all vendors. If an individual believes that a DoD covered entity CE is not complying with HIPAA. Best practices for breach prevent are.
Confidentiality integrity and availability are the fundamental objectives of health information security and the hipaa security rule requires covered entities and business associates to protect against threats and. Before you can prevent a data breach you need to know the sensitive data you collect store transmit or process. All of the above answer a.
Which of the following are breach prevention best practices. All of the above. PCs cell phones PDAs and the network says Pappas.
Select the best answer. Developing the IRP will help the IT staff of the company to control the data breach incidents. However these 30 best practices for preventing a data breach can reduce the risk and respond to an attack more effectively.
Which of the following are examples of personally identifiable information PII. Develop a Data Breach Response Plan. Companies that leveraged artificial intelligence machine learning analytics and automated.
All of the above. 7 Tips to Protect Your Business from Data Leaks. Promptly retrieve documents containing PHIPHI from the printer.
Monitor all network access. Access only the minimum amount of PHIpersonally identifiable information PII necessary. Which of the following are breach prevention best practices.
After the Development Checks of the Security Program. Create Strong Policies Strong Passwords. Access only the minimum amount of PHIpersonally identifiable information PII necessary.
Which of the following are breach prevention best practices. Logoff or lock your workstation when it is unattended C. What of the following are categories for punishing violations of federal health care laws.

Board Oversight Of Cyber Risks And Cybersecurity Imd Article

It Security Policy Key Components Best Practices For Every Business Bmc Software Blogs

Top 4 Human Errors In Cyber Security How To Prevent Employee Mistakes Ekran System
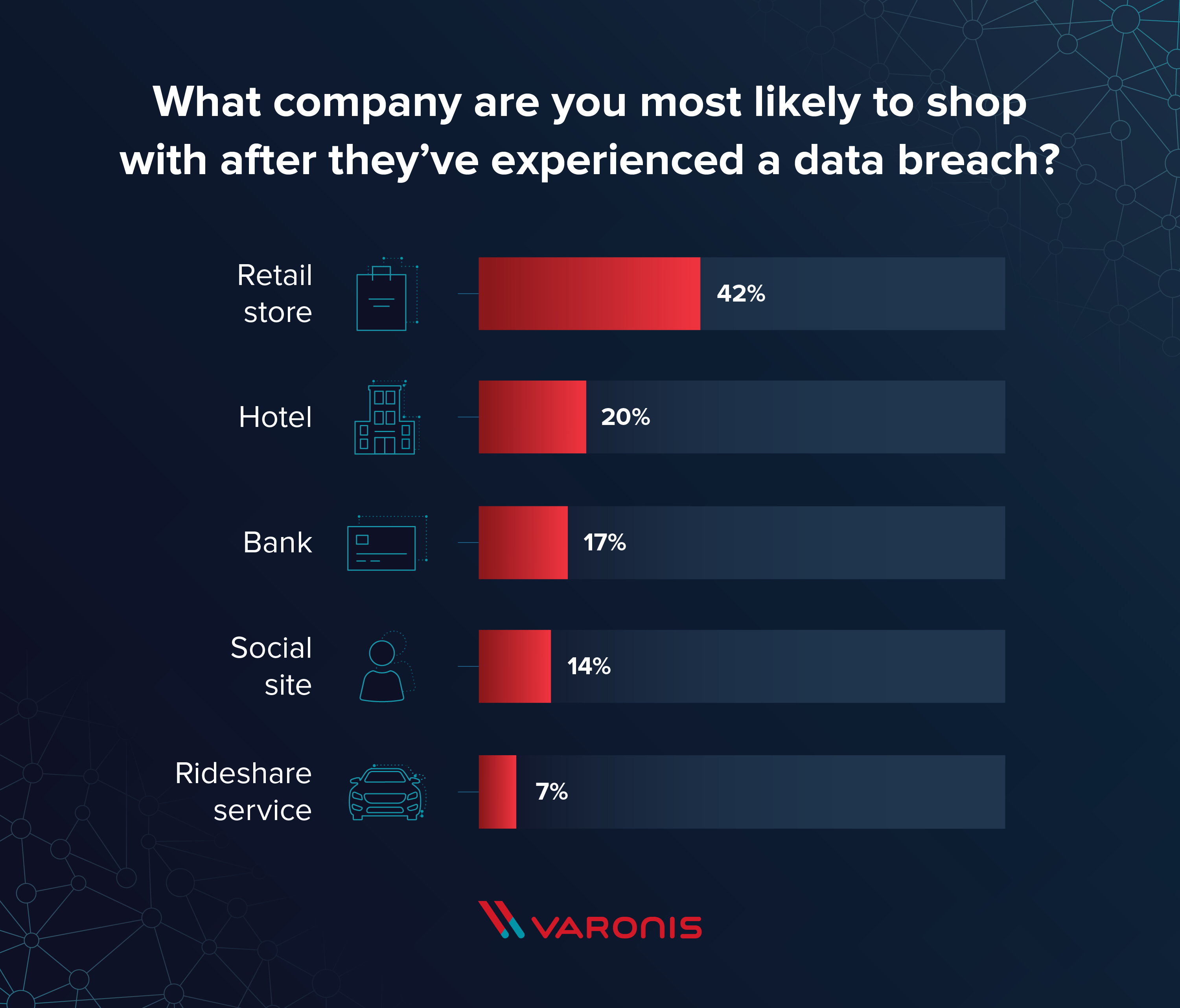
Analyzing Company Reputation After A Data Breach

6 Steps To Developing A Data Breach Response Plan Spectral

Preventing Hipaa Data Breaches Case Studies And Best Practices

Analyzing Company Reputation After A Data Breach

6 Most Common Causes Of Data Leaks In 2022 Upguard

Preventing Hipaa Data Breaches Case Studies And Best Practices

How To Prevent Data Breaches In 2022 Upguard

6 Most Common Causes Of Data Leaks In 2022 Upguard

Analyzing Company Reputation After A Data Breach

6 Enterprise Secure File Transfer Best Practices

Top 4 Human Errors In Cyber Security How To Prevent Employee Mistakes Ekran System